Link an Amazon Web Services account
Estimated reading time: 4 minutesYou can create a role with AWS IAM (Identity and Access Management) so that Docker Cloud can provision and manage node clusters and nodes on your behalf.
Previously, we recommended that you create a service user that Docker Cloud would use to access your AWS account. If you previously used this method, you can create a new role, attach the policy you created previously, unlink your AWS credentials and relink them using the new ARN method. You can then delete the dockercloud-user.
Create a dockercloud-policy
Create an access control policy that will grant specific privileges to Docker Cloud so it can provision EC2 resources on your behalf.
- Go to the AWS IAM panel at https://console.aws.amazon.com/iam/home#policies
- Click Create Policy.
- On the next screen click Create Your Own Policy.
-
Name the policy
dockercloud-policyand paste the following text in the space provided for Policy Document.{ "Version": "2012-10-17", "Statement": [ { "Action": [ "ec2:*", "iam:ListInstanceProfiles" ], "Effect": "Allow", "Resource": "*" } ] }To limit the user to a specific region, use the policy below instead.
ec2:*allows the user to perform any operation in EC2.iam:ListInstanceProfilesallows the user to retrieve instance profiles to apply to your nodes.Note: You cannot use an instance profile that has more permissions than the IAM user you are using with Docker Cloud. If you do that, you will get an “unauthorized operation” error. You can fix this issue by adding the
"Action":"iam:PassRole"permission to the policy for the service user. You can read more about this here - Click Validate Policy.
- If the validation is successful click Create Policy.
Limit dockercloud-policy to a specific EC2 region
You can use the following dockercloud-policy to limit Docker Cloud to a specific EC2 region. Replace the example region us-west-2 US West (Oregon) with the region you want.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"ec2:*"
],
"Effect": "Allow",
"Resource": "*",
"Condition": {
"StringEquals": {
"ec2:Region": "us-west-2"
}
}
},
{
"Action": [
"iam:ListInstanceProfiles"
],
"Effect": "Allow",
"Resource": "*"
}
]
}
Create a dockercloud-role role
- Go to the AWS IAM Role creation panel at https://console.aws.amazon.com/iam/home#roles
-
Give the new role a name, such as
dockercloud-role.Note: You must use one role per Docker Cloud account namespace, so if you will be using nodes from a single AWS account for multiple Docker Cloud accounts, you should add an identifying the namespace to the end of the name. For example, you might have
dockercloud-role-mobyanddockercloud-role-teamawesome. -
Select Role for Cross-Account Access, and in the submenu that opens select Allows IAM users from a 3rd party AWS account to access this account.
- In the Account ID field, enter the ID for the Docker Cloud service:
689684103426. -
In the External ID field, enter your Docker Cloud username.
If you’re linking to nodes for an organization, enter the organization name.
- Leave Require MFA unchecked.
- On the next screen, select the
dockercloud-policyyou created to attach to the role. -
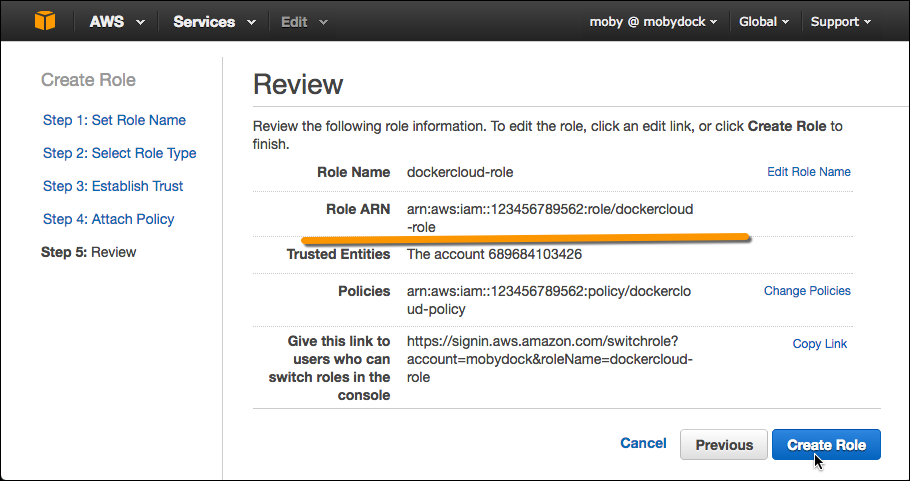
On next page review your entries and copy the full Role ARN string.
The ARN string should look something like
arn:aws:iam::123456789123:role/dockercloud-role. You’ll use the ARN in the next step. If you forget to copy the ARN here, view the Role in IAM to see its related information including the ARN. -
Click Create Role.

Add AWS account credentials
Once you’ve created the a dockercloud-policy, attached it to a
dockercloud-role, and have the role’s Role ARN, go back to Docker Cloud to connect the account.
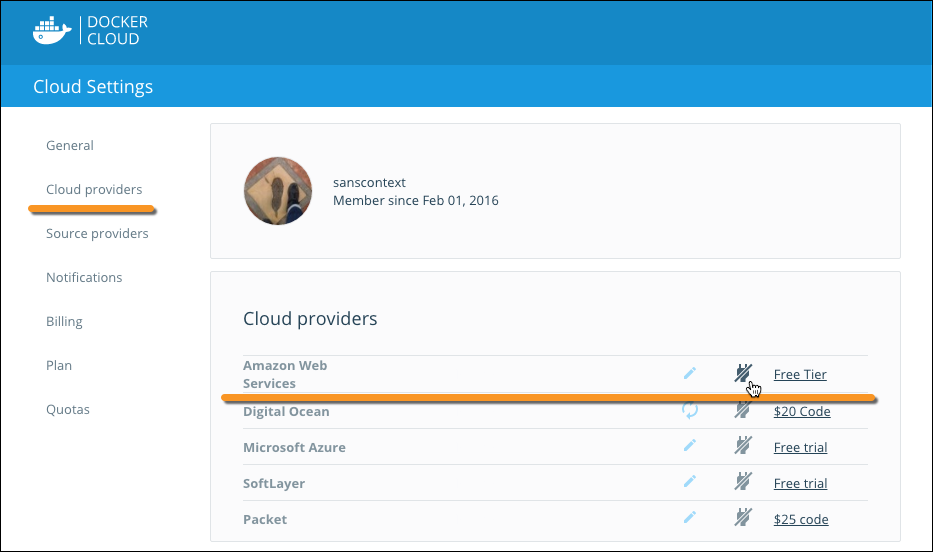
- In Docker Cloud, click Cloud settings at the lower left.
-
In the Cloud Providers section, click the plug icon next to Amazon Web Services.
-
Enter the full
Role ARNfor the role you just created.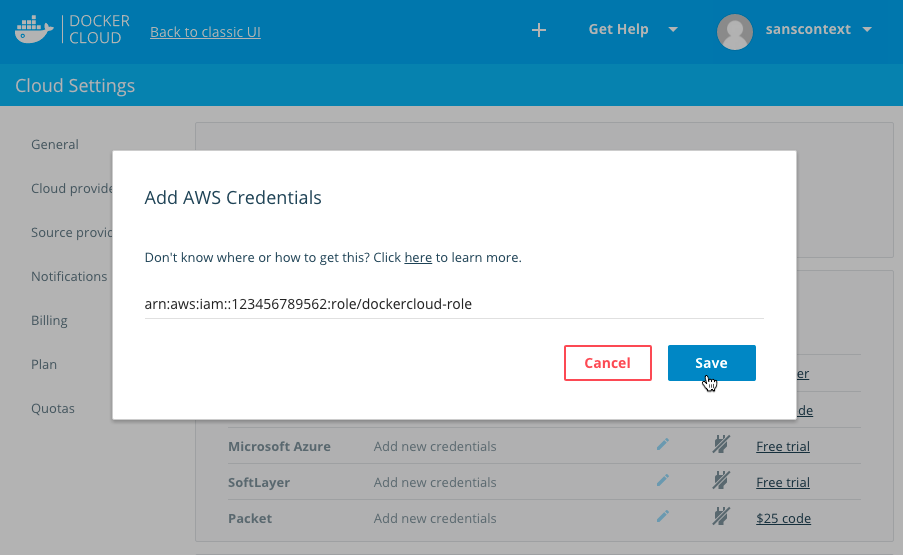
- Click Save.
What’s next?
You’re ready to start using AWS as the infrastructure provider for Docker Cloud! If you came here from the tutorial, click here to continue the tutorial and deploy your first node.
 Feedback? Suggestions? Can't find something in the docs?
Feedback? Suggestions? Can't find something in the docs?Edit this page ● Request docs changes ● Get support
Rate this page:
